Crafting a Website Compliant with HIPAA Standards in 2023

Enhance the Security of Your Healthcare Website: Adhere to the Guidelines Provided in This Manual for Ensuring HIPAA Compliance.
Explore the Importance of HIPAA Compliance in the Healthcare Sector and Uncover the Guidelines for Ensuring HIPAA-Compliant Websites in this Informative Article.
Jump To...

The healthcare sector is vast, with over $3 trillion expended annually within it. Given this immense financial scope, it’s unsurprising that the industry has attracted a notable contingent of cybercriminals and fraudsters seeking to pilfer patient information.
A web presence is pivotal for any organization, particularly in the medical field. As HIPAA compliance increasingly takes center stage, it’s crucial to grasp the essential terminology without feeling overwhelmed.
This guide aims to demystify what constitutes a HIPAA-compliant website and provide clarity on meeting all necessary requirements. By doing so, you can safeguard your business and shield yourself from potential legal repercussions.
Deciphering HIPAA Compliance for Your Website
Healthcare professionals must recognize that there isn’t a universal solution for HIPAA-compliant web hosting. However, grasping the fundamentals of HIPAA websites can empower any healthcare service provider to make informed choices regarding their site’s security and privacy. This entails comprehending the implications of HIPAA for your website and how to ensure compliance with this federal statute.
What Does HIPAA Stand For?
In the United States, protected health information can only be utilized and disclosed according to a series of government regulations referred to as the Health Insurance Portability and Accountability Act (HIPAA).
Both the Office for Civil Rights (OCR) and the Department of Health and Human Services (HHS) are responsible for upholding HIPAA compliance regulations (OCR). Healthcare enterprises must imbue a culture of HIPAA compliance across their operations to ensure the confidentiality, integrity, and accessibility of sensitive information.
What Constitutes Protected Health Information (PHI)?
Protected Health Information (PHI) encompasses any personally identifiable information directly tied to a patient’s healthcare. This includes details such as patients’ phone numbers, email addresses, compromised patient information, and the IP addresses of their devices. However, it’s important to note that any anonymous data collected through contact forms falls outside the scope of protected health information (PHI) and thus isn’t subject to HIPAA compliance requirements.
What does HIPAA mean for my website?
How you handle sensitive patient data and information can greatly impact the level of HIPAA compliance your website achieves. Hence, it’s crucial to grasp the implications of these regulations for your site before embarking on its development.
The Three Rules of HIPAA Compliance
Healthcare institutions are required to adhere to three primary HIPAA Compliance Rules: the HIPAA Privacy Rule, the HIPAA Security Rule, and the HIPAA Breach Notification Rule.
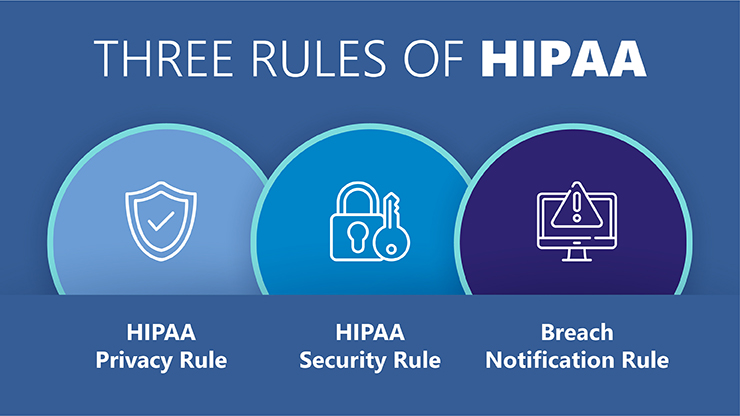
The HIPAA Privacy Rule governs the saving, accessing, and sharing of medical and personal information for any individual (ePHI). The HIPAA Security Rule establishes national security standards to safeguard electronic health records and related data, whether generated, obtained, preserved, or transferred. Conversely, Breach Notification Rules are tailored to address compromises in patient information.
The four main sections of the HIPAA Security Rule Standards and Implementation Specifications were crafted to outline essential security measures that uphold compliance.
These encompass physical measures (such as risk assessment and staff training), administrative protocols (including alarm and security systems), technical implementations (such as data encryption and audit controls), and policies and procedures documentation.
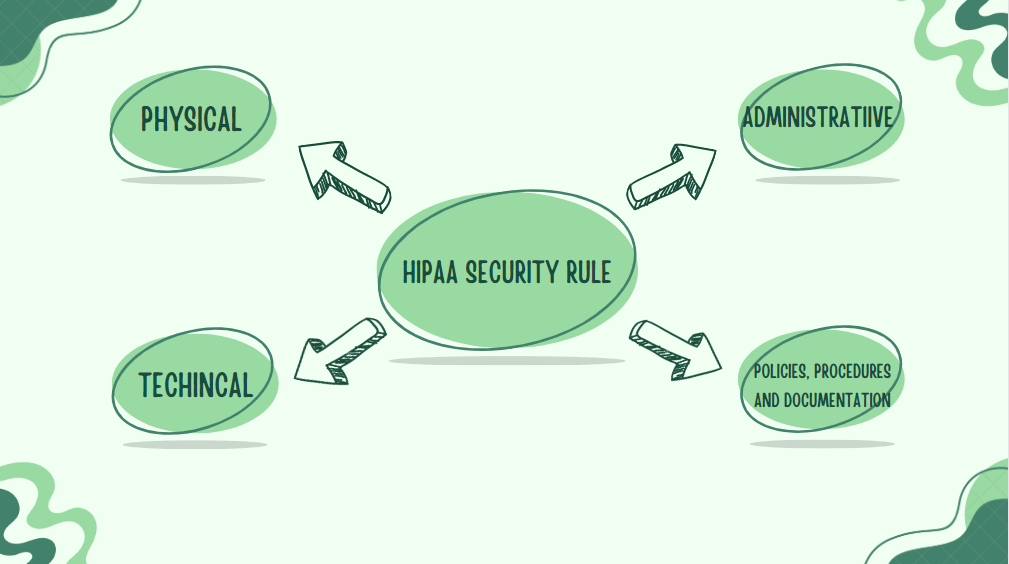
I have elaborated on the specifics of these four segments below:
1. Measures for physical security
Restricted facility entry and control with defined authorized access represent instances of physical protections. Every covered entity, or entity adhering to HIPAA regulations, needs access and usage regulations for computers and other electronic devices containing individually identifiable medical data. This includes actions like transferring, removing, discarding, and utilizing electronic media and protected health information.
2. Administrative safeguards
Risk assessment is a fundamental requirement of the Administrative Safeguards regulations concerning security management procedures for covered entities. Other obligations under the HIPAA enforcement rule for individuals engaged in health and human services include designating security personnel, managing information access, and more. Furthermore, healthcare professionals should ensure that their staff receive HIPAA compliance training.
3. Safeguards of a technical nature
The technical security measures that HIPAA-compliant organizations must adhere to under the Security Rule encompass:

Access control
All covered entities are required to establish technical policies and procedures that limit access to electronic Protected Health Information (PHI) only to authorized individuals, thus preventing any potential data breaches.
Audit controls
To monitor activity on hardware and software, audit reports or tracking logs must be implemented. This is especially beneficial for identifying the source or cause of any security breaches.
Integrity controls
Integrity controls, which are mechanisms established to verify that electronic Protected Health Information (ePHI) hasn’t been altered or deleted, are also addressed in technical policies. IT disaster recovery and offsite backup measures are crucial for preventing electronic media faults or failures.
Network security
According to this safeguard, HIPAA Compliant Hosts must enact technical policies and procedures that exclusively allow authorized individuals to access Electronic Protected Health Information (ePHI). This requirement extends to all methods of data transmission, encompassing email, the Internet, and even private networks such as private clouds.
Policies, Protocols, and Documentation
To comply with the security requirements, a HIPAA-Compliant host must enact policies and procedures that are deemed reasonable and appropriate.
Covered entities are required to maintain written security policies and procedures, along with written records documenting necessary actions, activities, or assessments. These records must be retained for a period of six years from their inception date or the final effective date, whichever is earlier.
Regular Refreshes
In response to changes in the organization’s culture or environmental factors that affect the storage of Protected Health Information (PHI), a covered entity must regularly assess and update its documentation, particularly electronic PHI (e-PHI).
What steps are necessary to ensure a website is compliant with HIPAA regulations?
A website that stores and transmits Protected Health Information (PHI) should adhere to HIPAA requirements. Healthcare companies must consider several factors, outlined below, to ensure their website is compliant with HIPAA regulations.

Below are the details of the sections outlined in your HIPAA Compliant Website Checklist:
HIPAA Privacy Rule
Your website must adhere to privacy regulations, which constitute a critical aspect of HIPAA security. This Privacy Rule is applicable to all hospitals, health plans, clearinghouses, and business associates.
Under this rule, safeguards must be implemented to protect Protected Health Information (PHI). Additionally, the rule outlines patients’ rights regarding their information, including the ability to request corrections and obtain copies of their health records.
Contracts with Business Associates
When entrusting your website to third-party service providers, you must sign a HIPAA Business Associate Agreement. This agreement ensures that your health information is encrypted and transmitted securely through a compliant website.
It’s important to note that while your web design team may have direct business connections, they might also engage subcontractors and other business associates who provide independent services.
Verify that your website possesses an SSL certificate.
To ensure secure communication between your site and its host, SSL (Secure Sockets Layer) is utilized. Consider the analogy: just as water can leak if a bag’s lid isn’t properly sealed, obtaining an SSL certificate is a crucial step to safeguard your data from malicious activities.
You must transition from the in secure HTTP protocol to the secure HTTPS protocol and implement a Secure Sockets Layer (SSL) or Transport Layer Security (TLS) encryption certificate for your website. This protocol encrypts all information transmitted between the client device and the server during secure user authentication.
Backups stored both onsite and offsite
Below are the explanation and importance of On-premises and Off-premises Backups:
Onsite Backups
An onsite backup refers to a system backup of data stored locally, typically conducted on the company’s premises.
Local backups provide protection against natural disasters, theft, and other types of calamities, ensuring data security and enabling disaster recovery, especially for companies heavily reliant on computer systems.
Offsite Backups
Offsite backups serve as a form of data protection, offering businesses access to a duplicate copy of production system data stored in a location distinct from the original data.
Replicating daily backups offsite provides a valuable disaster recovery tool. These replicated offsite backups are readily accessible and can be easily retrieved when restoration is needed.
Data Center Security and Audit Processes
Your healthcare service provider’s website must be secure and subject to audits. Beyond certifications related to healthcare laws, obtaining an audit based on the guidelines of the American Institute of Certified Public Accountants (AICPA), Statement on Standards for Attestation Engagements 18 (SSAE 18; previously SSAE 16), SOC 2, and SOC 3 can provide insight into the host’s security posture.
Managed Firewall
A managed firewall is another essential requirement for ensuring a HIPAA-compliant website. Key attributes of a well-managed firewall include strong security response capabilities, regular health checks for devices, monitoring logs, and control over network ingress and egress points.
Therefore, your online healthcare system should incorporate stateful filtering, global blacklisting, virtual private network (VPN) connectivity, load balancing, redundancy via a secondary firewall, as well as monitoring and reporting functionalities.
HIPAA Security Rule
Your HIPAA Compliant website must adhere to the HIPAA Security Rule, which sets forth an industry standard for safeguarding electronic medical records. The ePHI Act necessitates the implementation of reasonable physical, technical, and administrative safeguards to ensure that the organization can maintain patients’ Protected Health Information (PHI) in a secure ePHI environment. The most efficient approach to achieving HIPAA compliance entails conducting thorough research on web hosts.
HIPAA Compliant Website Platform
To ensure compliance with HIPAA regulations, it’s imperative to utilize a HIPAA-compliant website platform.
Security measures must be tailored to accommodate the various ways patients interact with your website. This concern is directly linked to electronic Protected Health Information (ePHI), regardless of how your company handles its creation, transmission, receipt, or maintenance.
When collecting information through forms on your website, it’s essential to ensure that HIPAA regulations protect all data. Any form gathering health information should safeguard the information against unauthorized online access and data breaches, similar to the protection provided for ePHI.
Infrastructure with a Focus on Healthcare
To ensure HIPAA compliance for your website, it’s imperative not to entrust your hosting to just anyone. HIPAA-compliant websites necessitate a high level of protection. Given the importance of security and compliance, it’s crucial to select an experienced web host that offers HIPAA-compliant solutions and compliance measures.
Choosing the right host is a critical initial step for organizations handling electronic Protected Health Information (ePHI). You need a host that is equally dedicated to upholding HIPAA Compliance rules and has implemented technical, administrative, and physical safeguards to demonstrate its commitment.
To begin, assess whether your hosting provider can deliver a website that meets the requirements of HIPAA and the Health Information Technology for Economic and Clinical Health (HITECH) Act of 2009.
Managed Multi-Factor Authentication
To ensure your website complies with HIPAA guidelines, it’s essential to implement sign-on access to a managed multi-factor authentication system. This system should conduct diagnostics on devices to ensure their health.
Regular checks for outdated programs and the implementation of security measures can prevent infected and high-risk devices from compromising security.
HIPAA compliance is a serious matter. If your site collects patients’ health information, you are responsible for safeguarding their personal data and privacy.
Navigating the standards governing this topic can be complex and confusing, as they are set by a body of regulations with specific language that must be followed to maintain compliance.
Fortunately, these standards do not frequently change. Once you have studied and understood them, you will have a framework to follow for the foreseeable future.
However, even after investing time and effort into creating a HIPAA-compliant website and preparing it for launch, it’s crucial to provide regular updates.
Working with qualified professionals, such as lawyers or web designers, is particularly important if your website will be utilized by medical services, facilities, health practitioners, or insurance companies.
Frequently Asked Questions
If you’re utilizing a website, you might need to adhere to HIPAA regulations regarding the collection of health information via forms.
Forms that solely request names, emails, or telephone numbers are generally unnecessary. However, if a form pertains to medical, insurance, or social security applications and requires health-related information, it must comply with HIPAA rules.
For HIPAA compliance, your website requires compliant tools. To ensure compliance, it’s essential to consider how your website will be utilized and how users can access it, as this affects their needs. Particularly, you’re concerned with electronic Protected Health Information (ePHI), whether it’s created, transmitted, received, or maintained by any organization.
When users submit a form on the site, it’s crucial to ensure that their information is secure. Any data collection form should be protected similarly to any electronic Protected Health Information (ePHI) to prevent unauthorized access and potential data leaks.
Healthcare providers must ensure that their website meets the requirements outlined by the Health Insurance Portability and Accountability Act (HIPAA). As indicated in the HIPAA-Compliant website checklist, every healthcare website must have robust protection measures in place. Clarity offers secure and dependable PHI security solutions for websites that adhere to HIPAA standards.